Format string finder uses binary ninja’s powerful IL’s to find format string vulnerabilities in binaries (without access to source code) and printf-like functions. It was featured in Paged Out!’s issue #1 winning Best Security/RE article leading to it being presented in São Paulo, Brasil at Hackers to Hackers Conference 2019.
You can find it here: https://github.com/Vasco-jofra/format-string-finder-binja or install it from Binary Ninja’s plugin manager.
Example
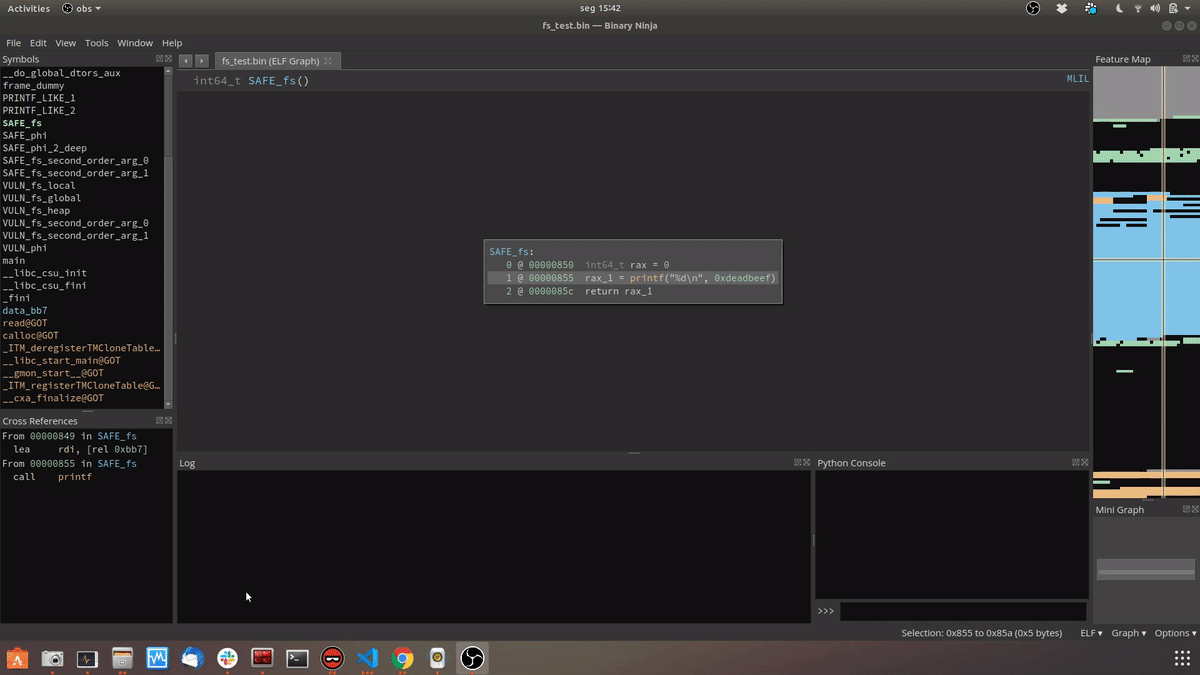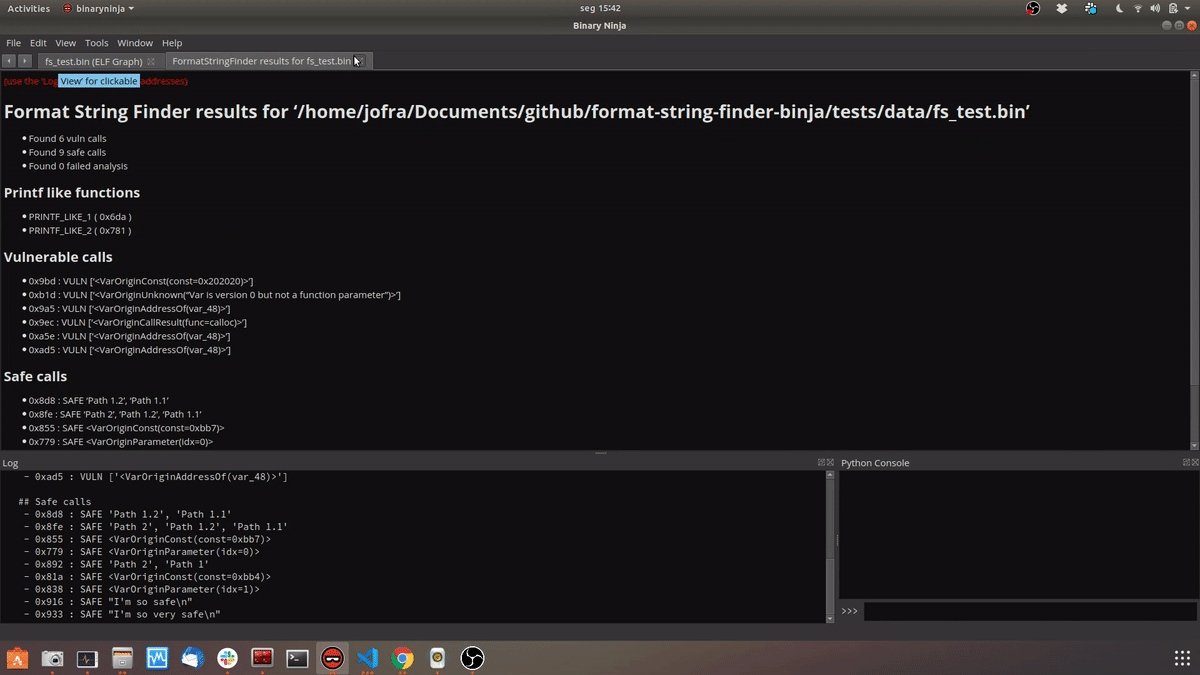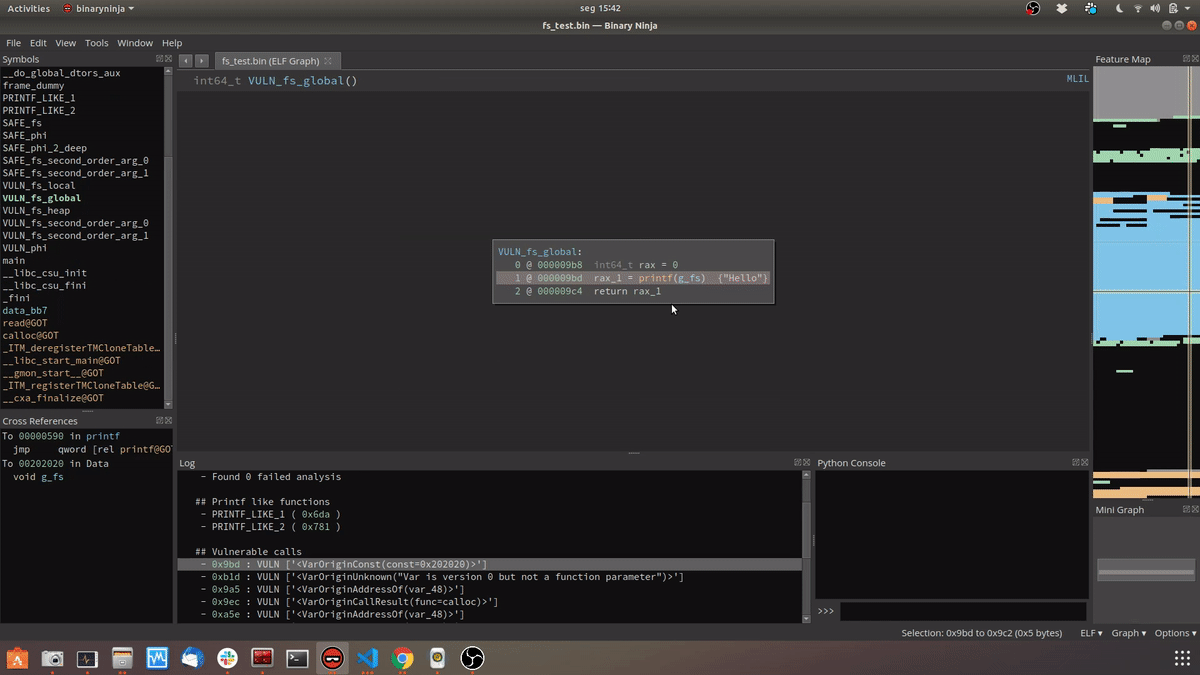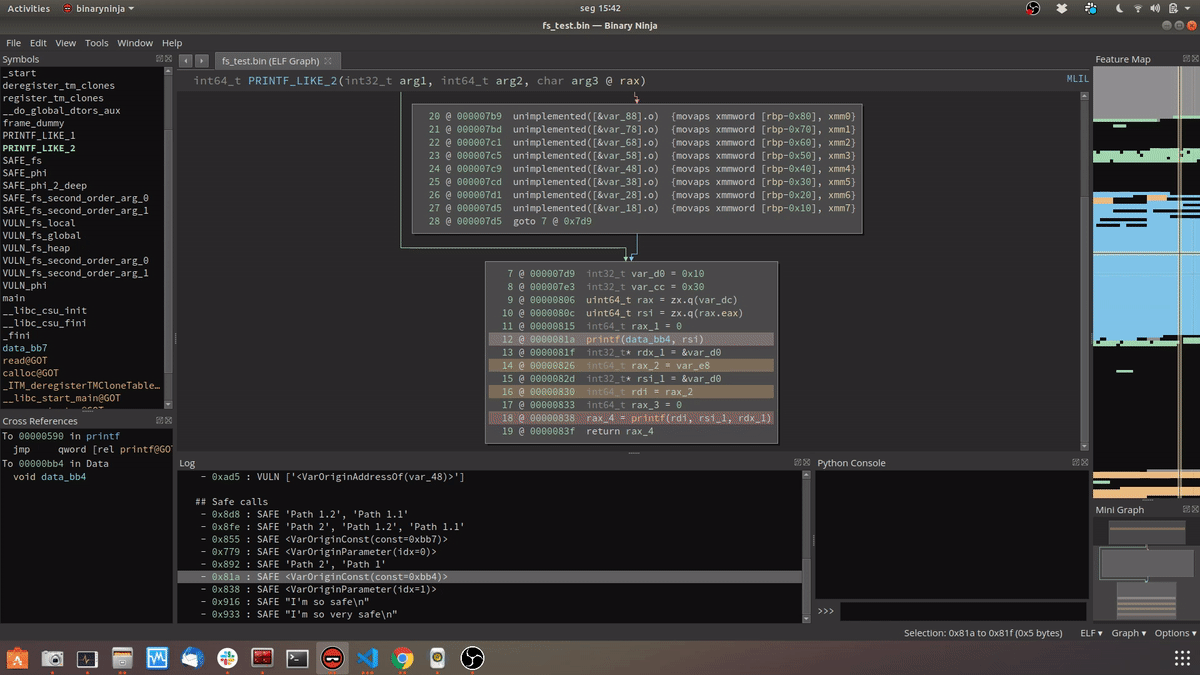
TL;DR
- Loads known functions that receive a format parameter.
- For each xref of these functions find where the fmt parameter comes from:
- If it comes from an argument we mark it as a printf-like function and test its xrefs
- If it is a constant value located in a read-only area we mark it as safe
- If it comes from a known ‘safe’ function call result (functions from the
dgettextfamily) we mark it as safe - Otherwise we mark it as vulnerable
- Prints a markdown report
Find out more in Paged Out!’s issue #1 at https://pagedout.institute/?page=issues.php.
